Organizations of all sizes in Thailand are moving towards digitalization and developing their own personal data protection systems to comply with the Personal Data Protection Act of 2019 (PDPA). The Cabinet approved postponing the full enforcement of the Thai Personal Data Protection Act (PDPA) for one further year due to the severe outbreak of COVID 19 in Thailand. Organizations then are looking for the robust, comprehensive, standard and easy to begin with solution.
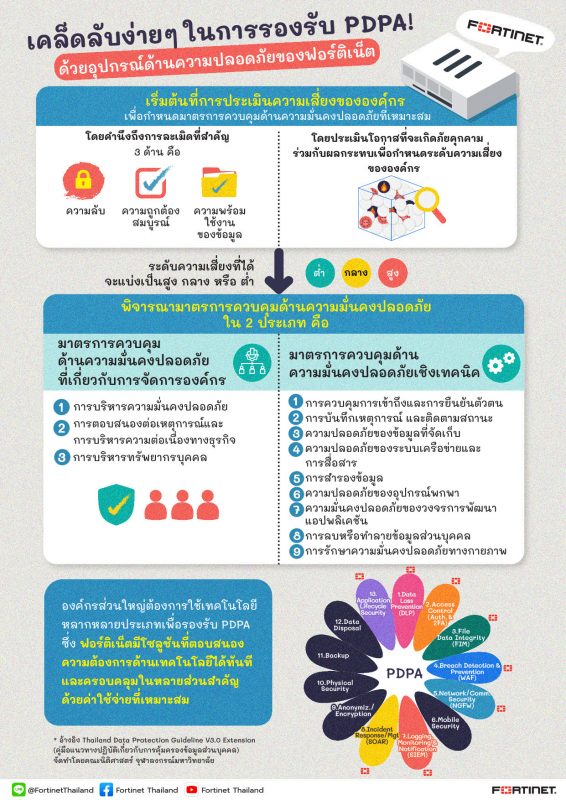
Referring to the Thailand Data Protection Guideline V3.0 Extension developed by the Faculty of Law at Chulalongkorn University guiding how organizations in Thailand can implement the granular personal data protection system, Fortinet recommends the organizations begin with Risk Assessment.
Risk assessment is an essential activity that helps the organizations to develop adequate measures in three aspects: confidentiality, integrity and high availability of the data. By assessing the threat occurrence probability together with the impact, the organization will obtain their risk level that can be high, medium or low. Such risk level then leads to the exercise to identify 3 strategic security pillars that are process, technology and human resources (people) appropriately for each area, to achieve the policy objectives determined by chief information security officer and security personnel.
Organizations should carefully evaluate suitable implementations that meet specific business requirements, compliance, and other related measure controls. The small and medium enterprises may consider designing additional granular security processes to technology and people pillars to help reduce the risk, such as establishing a clear definition of the right for high-privilege user accounts or least privilege access, and so on.
After security risk level assessment, the organizations will be able to define further appropriate organizational security measures and technical security measures. The organizational security measures shall include 3 strategic concerns, for instance. Firstly, security management covers the relevant policy and procedure guidance as well as roles and responsibilities, etc. definition. Secondly, the incident response and business continuity management are needed to handle the threat incidents and personal data breach events. Lastly, human resources management normally requires the organizations to provide their employees the regular information security training sessions and promoting secure environments, for example.
Technical measures can be defined as the measures and controls afforded to systems and any technological aspect of an organization, such as devices, networks and hardware. Protecting such aspects is crucial for the security of personal data and is the best line of defense against data breaches. Here are the most common technical measures the organizations should consider:
- Access control and authentication – Prevent the unauthorized access to information systems processing the personal data, and strictly control access using two-factor authentication (2FA) etc., for high-risk organizations.
- Logging and monitoring – Collect and monitor the user activities and files containing PII, to be used as evidence if any access, use, alteration, or modification occurs
- Security of data at rest – Protect stored data in computers, servers and database systems by deploying data encryption, etc.
- Network/communication security – Network security should be implemented regardless of the size and scope of your organisation. Firewalls, IPS, NAC as well as data encryption applications are cost effective and important.
- Back-ups – Backing up is an activity that allows an organization to recover corrupted data. High-risk organizations should consider more frequent backups and solid encryption for data stored in the backup device, etc.
- Mobile/portable devices – Prevent risks from mobile devices, smartphones or tablets by verifying your identity before using the device and encrypting personal data on mobile devices, as well as enforcing the security policies on mobiles.
- Application lifestyle security – Consider security to be deployed in the application lifecycle development, such as penetration test on applications and related systems as well as patching test evaluation before installing the actual patch, etc.
- Data deletion/disposal – Take measures to delete or destroy personal data to make it irrecoverable. It should be overwritten several times and destroy the storage device, for example.
- Physical security – Implement robust measures for securing access to any office or building and ensure that all employees are aware of such controls, which can include CCTV, security lighting and alarms in the zone that requires high security.
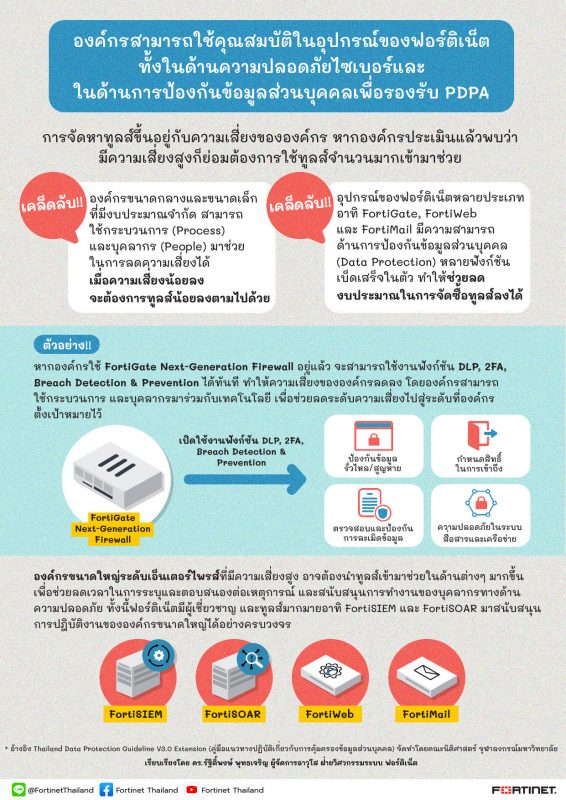
A frequently asked question to Fortinet is what additional tools or technologies organizations need to purchase? The answer is it depends upon the organization’s own risk level. The higher the risk, the more tools organizations will need to help. The small and medium-sized organizations with limited budgets may opt to establish the processes and people policy to help reduce the risk. Organizations with less risk require less tools as a result. Good news is many Fortinet security devices such as FortiGate, FortiWeb, or FortiMail contain data protection capabilities. Therefore, the organizations currently deploying Fortinet’s security appliances in complying to Cybersecurity Act (2019) or NIST, ENISA, ISO27001 frameworks, can deploy them for data protection purpose immediately. This empowers organizations to reduce their level of security risks and budget in tools procurement.
For example, a customer who is currently using the FortiGate Next-Generation Firewall together with additional technology and people resource programs, can turn DLP, 2FA, Breach Prevention functions to immediately reduce risks until reaching the acceptable level.
On the other hand, the large enterprises with high risk shall need more tools to help reduce the time spent on identifying, responding to incidents, and on supporting the overburdened security personnel in the organization. In this case, Fortinet provides tools such as FortiSIEM, FortiSOAR to support the granular operations of large enterprises.
It is admitted the impact and damage to business and corporate reputation is invaluable. Although the Cabinet has extended the enforcement deadline of the PDPA Act, organizations still have to accelerate the completion of PDPA solutions. You need to do your best to ensure the security of personal data you handle and be able to prove it. Fortinet can bring its experience, expertise and industry-leading products and services to help organizations meet the personal data protection requirement of the businesses of all types.
Source: Communication Arts